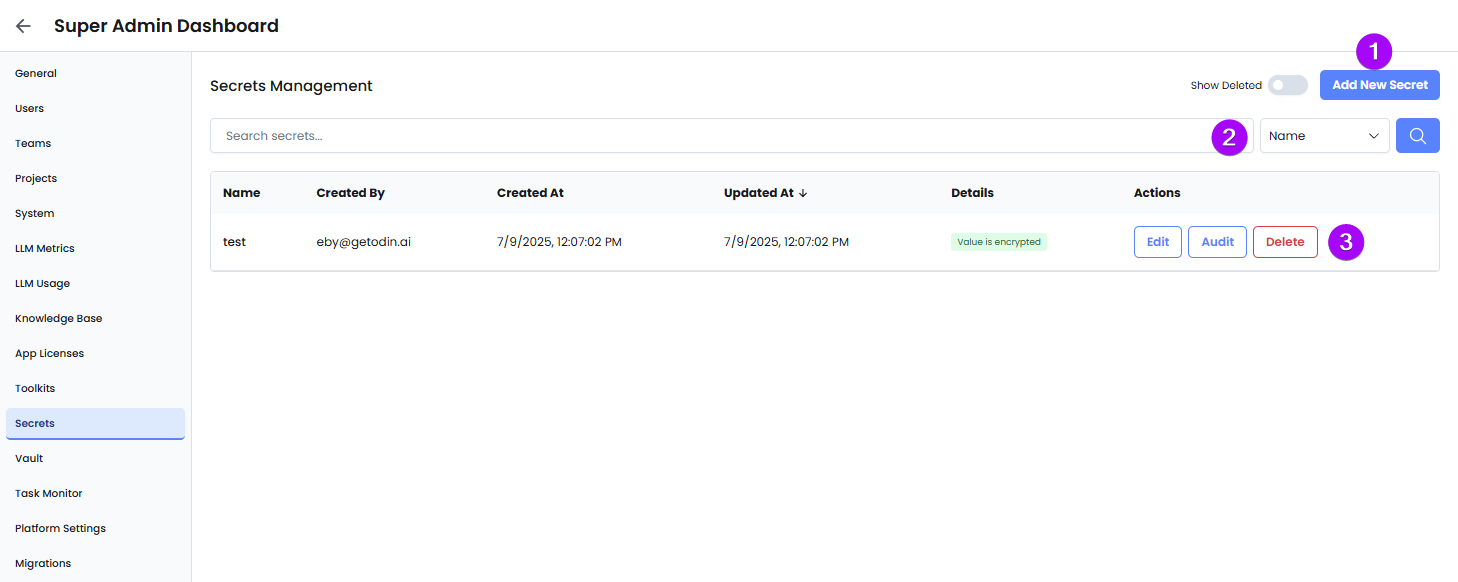
- Enter a name (e.g.,
OPENAI_API_KEY,SALESFORCE_TOKEN) - Paste the value of the secret (e.g., the token or key)
- Optionally tag the secret with relevant project scopes or usage contexts
- Use the search bar to quickly find a secret by its name or value.
- Use the dropdown filter to sort secrets (e.g., by name, creation date).
- Toggle Show Deleted to view secrets that were previously removed but may still be recoverable (if soft-deleted).
- Edit: Update the value (e.g., when rotating API keys).
- Delete: Remove secrets that are no longer in use (e.g., old staging credentials).
Best Practices
- Always use this tab to store keys or tokens—never paste them directly into logic blocks or agent configs.
- Use clear, consistent names like
ZAPIER_TOKEN,PROD_DB_PASS, orSLACK_WEBHOOK. - Periodically review and rotate secrets for security hygiene.
- Limit who can access and update secrets based on roles and project scope.
Example Use Case
Suppose you’ve built a customer support automation that needs to pull data from Salesforce. Instead of embedding your Salesforce API key directly into the automation:- Go to the Secrets tab.
- Add a new secret called
SALESFORCE_API_KEY. - Use that secret reference in the flow when authenticating with Salesforce’s API.

